[CEH V11]module1筆記
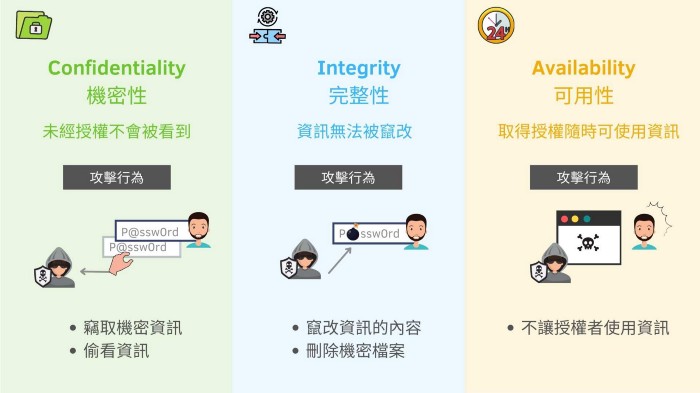
1.elements of information security(資安要素)
- Confidentiality 機密性
- Integrity 數據完整性-確保資料不會被串改
- Availability 可用性
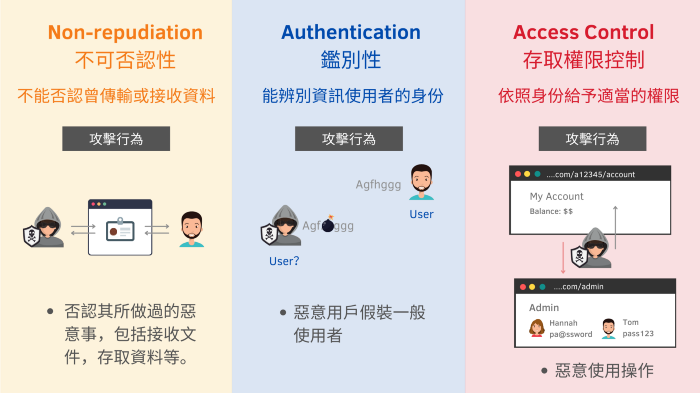
- Authenticity 真實性
- Accountability鑑別性
- Non-Repudiation 不可否認性

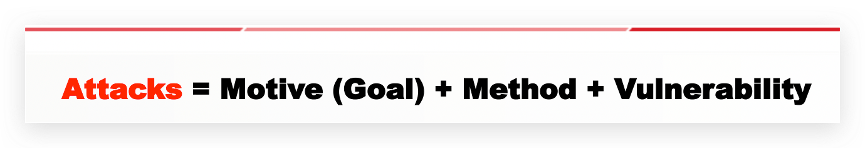
2.Motives, Goals & Objectives of Attacks攻擊的動機、目標和目的
下面公式要記得
| Disrupting business continuity | 破壞業務連續性 |
| stealing information and Manipulating data | 竊取信息和操縱數據 |
| Creating fear and chaos by disrupting critical infrastructures | 通過破壞關鍵基礎設施製造恐懼和混亂 |
| Causing financial loss to the target | 給目標帶來經濟損失 |
| Propagating religious or political beliefs | 傳播宗教或政治信仰 |
| Achieving a state’s military objectives | 實現國家的軍事目標 |
| Damaging the reputation of the target | 損害目標名譽 |
| Taking revenge | 報復 |
| Demanding ransom | 勒索 |
3.Classification of Attacks攻擊分類
- Passive Attacks 被動攻擊 -通常不直接接觸對方,只會monitoring network traffic 或是data flow 包含sniffing 和eavesdropping(監聽)
- Active Attacks
- Close-in Attacks 通常距離目標很近(但是你不是內部人員) 通常使用social engineering, including eavesdropping, shoulder surfing, dumpster diving, and other methods.
- Insider Attacks 就是個內賊
- Distribution Attacks 就是在設備生產或是安裝前就先埋好攻擊直接串改硬體或是軟體
4.Cyber Kill Chain methodology網絡殺傷鏈
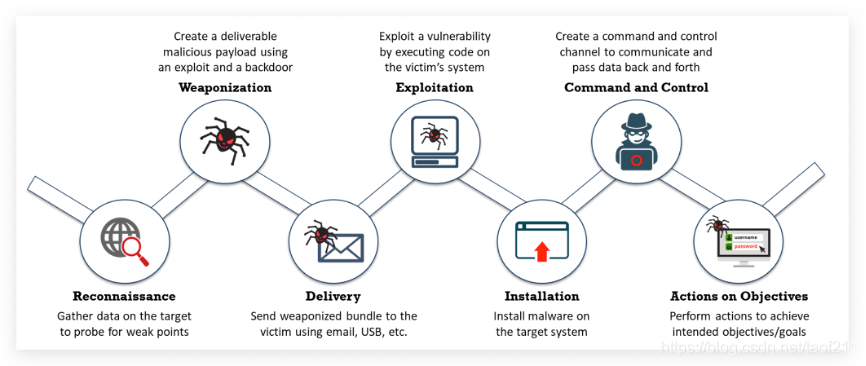
- Reconnaissance 偵查-先想辦法找出對方漏洞
- Weaponization武器化-把漏洞武器化
- Delivery運送-透過email 網路連結 usb等方式把惡意程式給目標物
- Exploitation-讓目標執行
- Installation-駭客在目標系統上下載並安裝更多的惡意軟體
- Command and Control
- Actions on Objectives上面已經可以控制受害者的系統了,即可以此為跳板來進入內部網路或是破壞更多的系統、獲取內部機密
5.Tactics(策略), Techniques, and Procedures (TTPs)
ttps是指patterns of activities and methods associated with specific threat actors or groups of threat actors(與特定威脅參與者或威脅參與者群體相關的活動模式和方法)其實我不是很了解這幾個是在幹嘛的就是…TTP就可以知道這群攻擊者常用的惡意程式類型、網域名稱,以及進駐到被害者電腦的方式。這類情資的價值比較高,因為當中會描述整個手法。
TTP 有助於分析威脅和剖析威脅參與者,並可進一步用於加強組織的安全基礎設施。
- Tactics-描述了威脅行為者在攻擊的不同階段的運作方式
- Techniques-攻擊者攻擊方法
- Procedures-威脅行為者執行的一系列動作

6.Adversary Behavioral Identification對手行為識別
了解駭客發起攻擊或是滲透的常見方法及技術,可以幫助安全人員了解及將到的威脅及漏洞,以下是依些常見的漏洞
| Internal Reconnaissance | 內部偵察 |
| Use of PowerShell | 使用 PowerShell |
| Unspecified Proxy Activities | 未指定的代理活動 |
| Use of Command-Line Interface | 使用cmd |
| HTTP User Agent | HTTP 用戶代理 |
| Command and Control Server | 命令和控制服務器 |
| Use of DNS Tunneling | 使用 DNS 隧道 |
| Use of Web Shell | 使用 Web Shell |
| Data Staging | 數據暫存 |
7. Indicators of Compromise (IoCs)入侵指標
所謂的IOC,不只是包含IP位址、網域名稱,還有一些clues(線索), artifacts(文物), and pieces of forensic data(法醫證據)等等,IoC 不是智能。相反,IoC 充當了有關威脅的良好訊息來源,在情報過程中充當數據點。從 IoC 中提取的可操作威脅情報可幫助組織增強事件處理策略。因此IoC可以分為以下四類
- Email Indicators
- Network Indicators
- Host-Based Indicators
- Behavioural Indicators(行為指標)
8.What is Hacking?什麼是黑客攻擊?
Hacking in the field of computer security refers to exploiting system vulnerabilities and compromising security controls (黑客攻擊是指利用系統漏洞和危害安全控制)
It involves modifying system or application features to achieve a goal outside its creator’s original purpose. (它涉及修改系統或應用程序功能以實現其創建者最初目的之外的目標。)
9.Hacker Classes駭客分類
- Black Hats
- White Hats – 不破壞的駭客
- Gray Hats – 白天上班做資安,晚上去打客戶網站
- Suicide Hats
- Script Kiddies – 就是指會用腳本工具的小鬼,沒任何技巧
- Cyber Terrorists – 網路恐怖主義-利用網路攻擊造成生命威脅等,像是玩命關頭的賽芙這種
- State-Sponsored Hackers– 國家級的駭客拉
- Hacktivist
10.Hacking Phase 黑客階段
- Reconnaissance 偵察
- Scanning 掃描
- Gaining Access 提權-包含破密、session jijacking來提升作業系統、軟體或是網路權限
- Maintaining Access維持權限-可以透過backdoors rootkits trojans等方式
- Clearing Tracks清除軌跡
11.Why Ethical Hacking is Necessary為什麼道德黑客是必要的
- To prevent hackers from gaining access to the organization’s information systems(防止駭客訪問組織的系統)
- To uncover vulnerabilities in systems and explore their potential as a risk(發現系統中的漏洞並探索其潛在風險)
- To analyze and strengthen an organization’s security posture, including policies, network protection infrastructure, and end-user practices(分析和加強組織的安全狀況,包括政策、網絡保護基礎設施和最終用戶實踐)
- To provide adequate preventive measures in order to avoid security breaches(提供足夠的預防措施以避免安全漏洞)
- To help safeguard the customer data(幫助保護客戶數據)
- To enhance security awareness at all levels in a business(提高企業各個層面的安全意識)
12.Scope & Limitation of Ethical Hacking道德黑客的範圍和限制
道德駭客 is a crucial component of risk assessment(風險評估), auditing(審計), counter fraud
(反欺詐), and information systems security (訊息系統安全) best practices.
It is used to identify risks and highlight remedial actions(高風險行動). It is also used to reduce Information and Communications Technology (ICT) costs by resolving vulnerabilities.(它還用於通過解決漏洞來降低信息和通信技術 (ICT) 成本)
13.Skills of an Ethical Hacker道德黑客的技能(看看就好)
1.Technical Skills技術能力
- In-depth knowledge of major operating environments, such as Windows, Unix, Linux, and Macintosh
- In-depth knowledge of networking concepts, technologies, and related hardware and software
- A computer expert adept at technical domains
- The knowledge of security areas and related issues
- High technical knowledge of how to launch sophisticated attacks
2.Non-Technical Skills非技術技能
- The ability to quickly learn and adapt new technologies
- A strong work ethic and good problem solving and communication skills
- Commitment to an organization’s security policies
- An awareness of local standards and laws
Information Assurance (IA)訊息保障
IA refers to the assurance of the integrity(數據完整性), availability(可用性), confidentiality(機密性), and authenticity(真實性) of information and information systems during the usage, processing, storage, and transmission of information(簡單來說 就是來保障資安三(五)要素用的)
- Developing local policy, process, and guidance
- Designing network and user authentication strategies
- Identifying network vulnerabilities and threats
- Identifying problems and resource requirements
- Creating plans for identified resource requirements
- Applying appropriate information assurance controls
- Performing the Certification and Accreditation
- Providing information assurance training
Defense-in-Depth縱深防禦
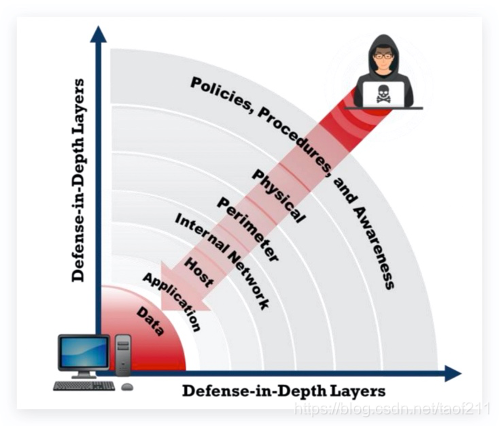
中間跳過0rz..
這邊太無聊了
Information Security Laws & Standards安全法律與標準
下面是常見的幾種標準法律,當然還有各國的法律就不列了
- Payment Card Industry Data Security Standard (PCI DSS)線上金流法案
- ISO/IEC 27001:2013 資訊安全管理系統規範
- Health Insurance Portability and Accountability Act (HIPAA)醫療資訊法案
- Sarbanes Oxley Act (SOA)沙賓法案-內線交易法案
- The Digital Millennium Copyright Act (DMCA) 這個常在google的一定看過數位著作權法案
- The Federal Information Security Management Act (FISMA)美國聯邦資訊安全管理法-資訊安全管理法案
The HIPAA Security Rule establishes national standards to protect individuals’ electronic personal health information that is created, received, used, or maintained by a covered entity. The Security Rule requires appropriate administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and security of electronically protected health information.
參考資料
- https://blog.csdn.net/taof211/article/details/110219994
- CEH v11 笔记总结 Module 1 (B)
- CEH v11 笔记总结 Module 1 (C)
- 危害指標(Indicator of compromise)




太讚了!